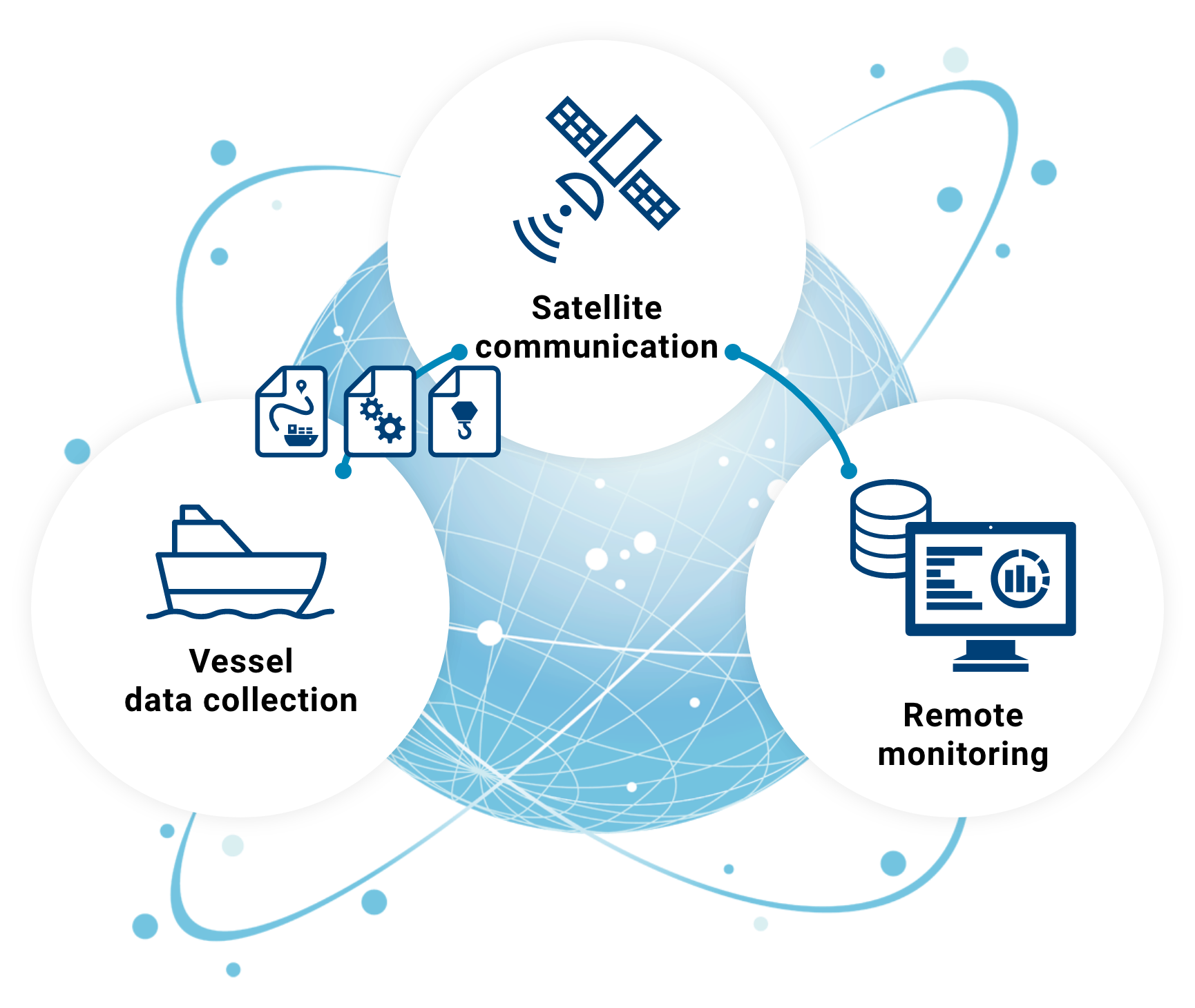
Imagine this: You're stuck in a situation where you need to access your office computer from home, but there's this big, scary thing called a "firewall" blocking your way. Sounds familiar? Well, fear not, because we're diving deep into the world of remote control devices behind firewalls. In this article, we'll break it all down for you—what it means, how it works, and most importantly, how you can get it done without losing your mind.
Remote control device behind firewall isn't just some tech jargon—it's a real-world solution that's becoming increasingly important in today's work-from-anywhere culture. Whether you're an IT pro, a remote worker, or just someone who wants to access their stuff from afar, understanding this concept is key to staying productive and secure.
So, buckle up, because we're about to take you on a journey through the ins and outs of remote control devices behind firewalls. By the end of this guide, you'll be equipped with the knowledge and tools to make remote access work for you, no matter where you are. Let's get started!
Read also:Robert Low Prime Inc Net Worth The Untold Story Of Success And Wealth
Table of Contents
What is Remote Control Device Behind Firewall?
Security Concerns and Best Practices
Read also:Wwe Nip Slips The Controversies Stories And Everything You Need To Know
Setting Up Remote Access Behind Firewalls
What is Remote Control Device Behind Firewall?
Let's start with the basics. A remote control device behind firewall is essentially a setup that allows you to remotely access and control a device, like a computer or server, even when it's protected by a firewall. Think of it like trying to unlock a door that's behind a really tough security system. The firewall is there to keep unwanted visitors out, but with the right tools and techniques, you can still gain access when you need to.
Now, why would you want to do this? Well, there are plenty of reasons. Maybe you're a system admin who needs to troubleshoot issues on a server from home. Or perhaps you're an employee who forgot an important file on your office computer. Whatever the reason, being able to remotely access your devices is a game-changer in today's fast-paced world.
Breaking Down the Concept
At its core, remote control involves using software or hardware solutions to establish a connection between your device and the target device. The tricky part is doing this securely when firewalls are in place. Firewalls are designed to block unauthorized access, so getting around them requires some clever solutions.
Some common methods include setting up virtual private networks (VPNs), using port forwarding, or leveraging cloud-based services. Each method has its pros and cons, and we'll dive deeper into them later. But for now, just know that it's definitely possible to control devices remotely even when firewalls are involved.
Why is It Important?
In today's digital landscape, remote work has become the norm for many industries. With that comes the need for secure and reliable ways to access work resources from anywhere. That's where remote control device behind firewall comes into play. It's not just a nice-to-have feature—it's essential for maintaining productivity and efficiency.
For businesses, enabling remote access can lead to cost savings, improved employee satisfaction, and better disaster recovery options. Employees can work from home, travel, or even access critical systems during emergencies without missing a beat. And let's not forget the security aspect. By setting up proper remote access protocols, companies can ensure that sensitive data remains protected while still allowing authorized users to access it.
Key Benefits
- Increased productivity for remote workers
- Cost savings on office space and resources
- Enhanced flexibility for employees
- Improved disaster recovery capabilities
- Stronger security measures
How Does It Work?
Now that we know what remote control device behind firewall is and why it's important, let's talk about how it actually works. The process involves several key components, including the remote client, the host device, and the network infrastructure. Here's a step-by-step breakdown:
- Remote Client: This is the device you'll be using to access the host device. It could be your laptop, smartphone, or tablet.
- Host Device: This is the device you want to control remotely, such as your office computer or a server.
- Network Infrastructure: This includes the firewall, routers, and other network components that connect the two devices.
When you initiate a remote connection, the remote client sends a request to the host device through the network. The firewall then evaluates the request based on predefined rules and either allows or denies access. If access is granted, a secure connection is established, allowing you to control the host device as if you were sitting right in front of it.
Common Protocols
There are several protocols used for remote control, each with its own strengths and weaknesses. Some of the most popular ones include:
- Remote Desktop Protocol (RDP): A Microsoft-developed protocol that allows users to remotely access Windows-based systems.
- Virtual Network Computing (VNC): A platform-independent protocol that supports remote access across different operating systems.
- SSH (Secure Shell): A protocol primarily used for secure command-line access to remote systems.
Security Concerns and Best Practices
While remote control device behind firewall offers numerous benefits, it also comes with its share of security concerns. After all, you're essentially opening a door into your network, which can be a tempting target for hackers. That's why it's crucial to follow best practices to ensure your setup is as secure as possible.
Some of the top security concerns include unauthorized access, data breaches, and malware infections. To mitigate these risks, you should:
- Use strong, unique passwords for all remote access accounts.
- Enable multi-factor authentication (MFA) whenever possible.
- Regularly update your software and firmware to patch vulnerabilities.
- Monitor network activity for suspicious behavior.
By implementing these measures, you can significantly reduce the chances of a security breach and protect your valuable data.
Firewall Rules
Firewall rules play a critical role in securing remote access. These rules determine which traffic is allowed or denied through the firewall. It's important to configure these rules carefully to strike a balance between security and usability.
Some best practices for firewall rules include:
- Limiting access to specific IP addresses or ranges.
- Restricting access to certain ports or protocols.
- Regularly reviewing and updating firewall rules to reflect changing needs.
Top Tools for Remote Control
There are countless tools available for remote control device behind firewall, each with its own features and capabilities. Choosing the right one depends on your specific needs and budget. Here are some of the top options currently available:
1. TeamViewer
TeamViewer is a popular choice for remote control due to its ease of use and robust feature set. It supports cross-platform access, file transfer, and even unattended access for servers.
2. AnyDesk
AnyDesk is another excellent option that offers high-speed connections and strong encryption. It's great for both personal and professional use.
3. LogMeIn
LogMeIn is a well-established player in the remote access space, offering a wide range of features for businesses of all sizes. It's particularly useful for managing multiple devices.
Understanding Firewalls
Before we dive into the specifics of setting up remote access behind firewalls, it's important to have a solid understanding of what firewalls are and how they work. Firewalls are essentially security systems that monitor and control incoming and outgoing network traffic based on predetermined rules.
There are several types of firewalls, including:
- Packet Filtering Firewalls: These firewalls examine individual packets of data and either allow or deny them based on certain criteria.
- Stateful Inspection Firewalls: These firewalls keep track of the state of network connections and use that information to make more informed decisions.
- Application-Level Gateways: These firewalls operate at the application layer, providing more granular control over specific applications and services.
Understanding the type of firewall you're working with is key to successfully setting up remote access.
Setting Up Remote Access Behind Firewalls
Now that we've covered the basics, let's talk about the actual setup process. Setting up remote access behind firewalls can seem intimidating, but with the right guidance, it's definitely doable. Here's a step-by-step guide:
- Choose Your Remote Access Tool: Select a tool that best fits your needs and budget.
- Configure Firewall Rules: Set up the necessary rules to allow remote access while maintaining security.
- Install and Configure the Software: Install the remote access software on both the client and host devices and configure it according to your requirements.
- Test the Connection: Once everything is set up, test the connection to ensure it's working properly.
Remember, the key to a successful setup is thorough planning and attention to detail. Don't rush the process, and always double-check your settings to avoid potential issues.
Troubleshooting Common Issues
Even with the best planning, issues can still arise when setting up remote access behind firewalls. Some common problems include connection timeouts, authentication failures, and network connectivity issues. Here are some tips for troubleshooting:
- Check Firewall Rules: Ensure that the necessary rules are in place and correctly configured.
- Verify Software Settings: Double-check that the remote access software is properly installed and configured on both devices.
- Test Network Connectivity: Use tools like ping or traceroute to diagnose network issues.
If all else fails, consult the documentation for your chosen remote access tool or reach out to their support team for assistance.
The Future of Remote Access
As technology continues to evolve, so too does the landscape of remote access. Emerging trends like cloud-based solutions, AI-driven security, and quantum encryption promise to revolutionize the way we access and control devices remotely.
Cloud-based remote access solutions, for example, offer increased flexibility and scalability, making it easier than ever to manage remote access across multiple devices and locations. Meanwhile, AI-driven security systems can detect and respond to threats in real-time, providing an extra layer of protection for your network.
Looking ahead, the future of remote access is bright. With the right tools and strategies in place, businesses and individuals alike can harness the power of remote control device behind firewall to stay productive, secure, and connected in an increasingly digital world.
Wrapping It Up
And there you have it—the ultimate guide to mastering remote control device behind firewall. From understanding the basics to setting up your own remote access system, we've covered everything you need to know to get started. Remember, remote access isn't just about convenience—it's about staying connected, productive, and secure in today's fast-paced world.
So, what are you waiting for? Take action now by trying out some of the tools and techniques we've discussed. And don't forget to leave a comment or share this article with your friends and colleagues who might find it useful. Together, let's make remote access a breeze for everyone!